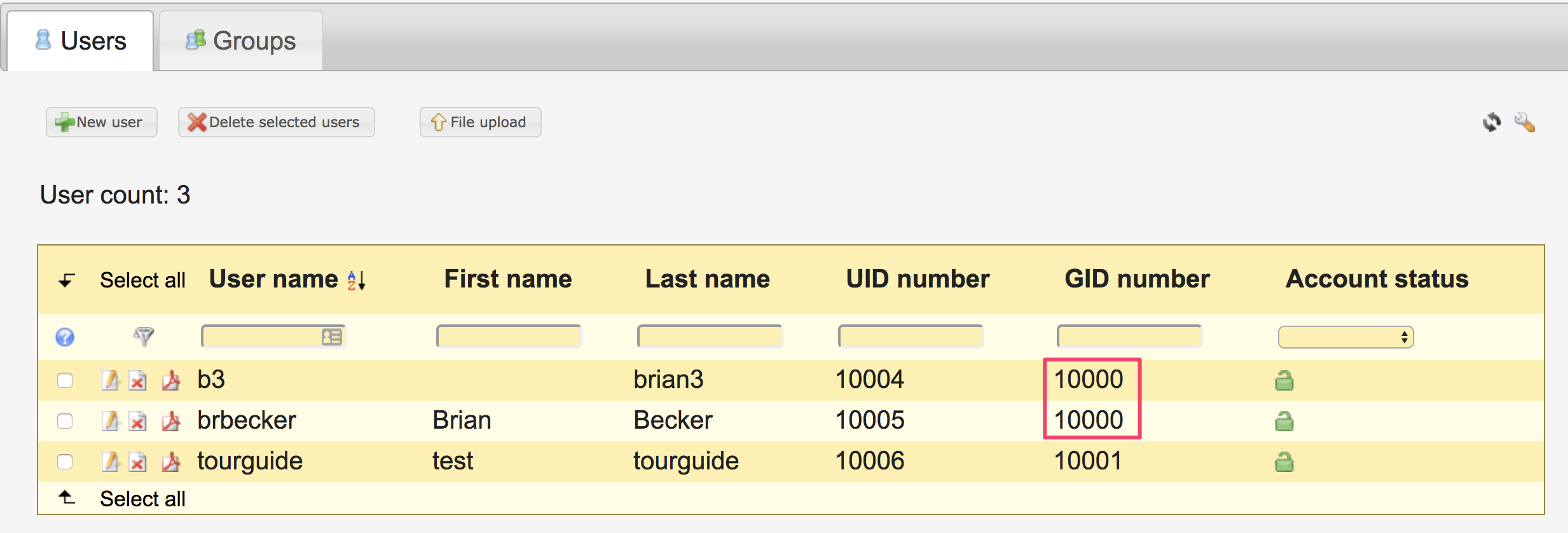
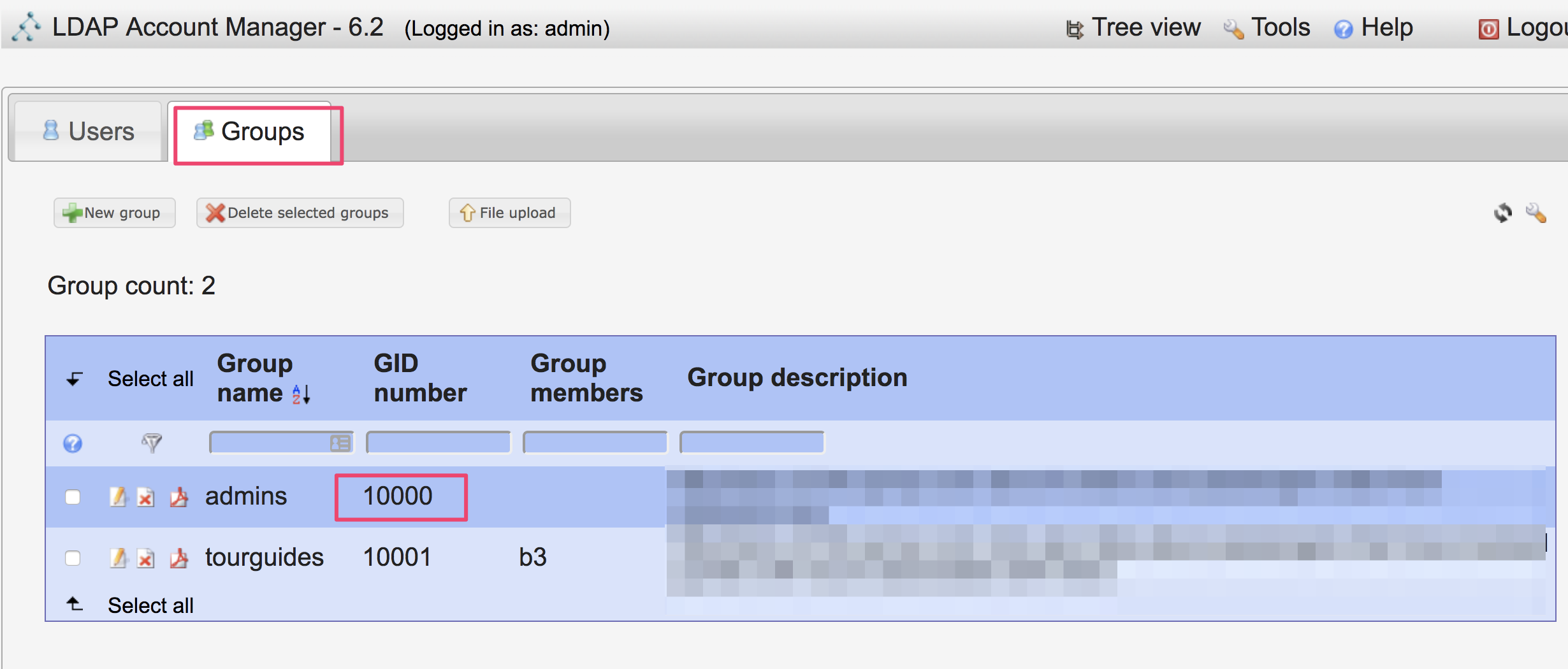
Hi @fmichielssen,
I’ve been struggling with the same issue of having no “roles” for hours now and am stuck. I can authenticate users but I really am hoping to get the group authorizations working correctly. I’m pretty new to LDAP as well.
Here’s the ldap portion of my application.yml file:
url: ldap://localhost:389/dc=xxx,dc=xxx,dc=com
manager-dn: cn=admin,dc=xxx,dc=xxx,dc=com
manager-password: "xxx"
user-search-filter: uid={0}
user-search-base: ou=People
group-search-base: ou=group
group-search-filter: (uniqueMember={0})
I exported my LDAP tree structure here as a text file:
# Search scope: sub
# Search filter: (objectClass=*)
# Total entries: 12
#
# Generated by LDAP Account Manager (http://www.ldap-account-manager.org) on December 31, 2018 12:44 am
# Version: 6.2
version: 1
# Entry 1: dc=xxx,dc=xxx,dc=com
dn: dc=xxx,dc=xxx,dc=com
dc: test
o: xxx
objectclass: top
objectclass: dcObject
objectclass: organization
# Entry 2: cn=admin,dc=xxx,dc=xxx,dc=com
dn: cn=admin,dc=xxx,dc=xxx,dc=com
cn: admin
description: LDAP administrator
objectclass: simpleSecurityObject
objectclass: organizationalRole
userpassword: {SSHA}oVaJmDmHSVEEP/j5hoLBZvA2bTf77xzd
# Entry 4: ou=group,dc=xxx,dc=xxx,dc=com
dn: ou=group,dc=xxx,dc=xxx,dc=com
objectclass: organizationalUnit
ou: group
# Entry 5: cn=admins,ou=group,dc=xxx,dc=xxx,dc=com
dn: cn=admins,ou=group,dc=xxx,dc=xxx,dc=com
cn: admins
description: want these to be admin users in shinyproxy
gidnumber: 10000
objectclass: posixGroup
# Entry 8: cn=tourguides,ou=group,dc=xxx,dc=xxx,dc=com
dn: cn=tourguides,ou=group,dc=xxx,dc=xxx,dc=com
cn: tourguides
description: want these to be my non admin users
gidnumber: 10001
objectclass: posixGroup
# Entry 9: ou=People,dc=xxx,dc=xxx,dc=com
dn: ou=People,dc=xxx,dc=xxx,dc=com
objectclass: organizationalUnit
ou: People
# Entry 10: uid=b3,ou=People,dc=xxx,dc=xxx,dc=com
dn: uid=b3,ou=People,dc=xxx,dc=xxx,dc=com
cn: b3
gidnumber: 10000
homedirectory: /home/b3
loginshell: /bin/bash
objectclass: posixAccount
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
sn: brian3
uid: b3
uidnumber: 10004
userpassword: {SSHA}Amf0ZvdtgRzhrINABQr9ZBP5djZxcHF1
# Entry 11: uid=brbecker,ou=People,dc=xxx,dc=xxx,dc=com
dn: uid=brbecker,ou=People,dc=xxx,dc=xxx,dc=com
cn: Brian Becker
gidnumber: 10000
givenname: Brian
homedirectory: /home/brbecker
loginshell: /bin/bash
objectclass: posixAccount
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
sn: Becker
uid: brbecker
uidnumber: 10005
userpassword: {SSHA}41opjog77lsi0pkJ2CEiXZyAKEBqUXQ1
# Entry 12: uid=tourguide,ou=People,dc=xxx,dc=xxx,dc=com
dn: uid=tourguide,ou=People,dc=xxx,dc=xxx,dc=com
cn: test tourguide
gidnumber: 10001
givenname: test
homedirectory: /home/tourguide
loginshell: /bin/bash
objectclass: posixAccount
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
sn: tourguide
uid: tourguide
uidnumber: 10006
userpassword: {SSHA}K7Eu/fpWpWXllUb7wm3AglO/+FxXc0ZY
I would think I need to adjust the group-search-filter field in the application.yml file? Maybe my groups don’t have an attribute called uniqueMember?
I appreciate any help!!