I’ve got a shinyproxy solution deployed via kubernetes to https://shinyserver.stephlocke.com
I have Azure AD B2C setup 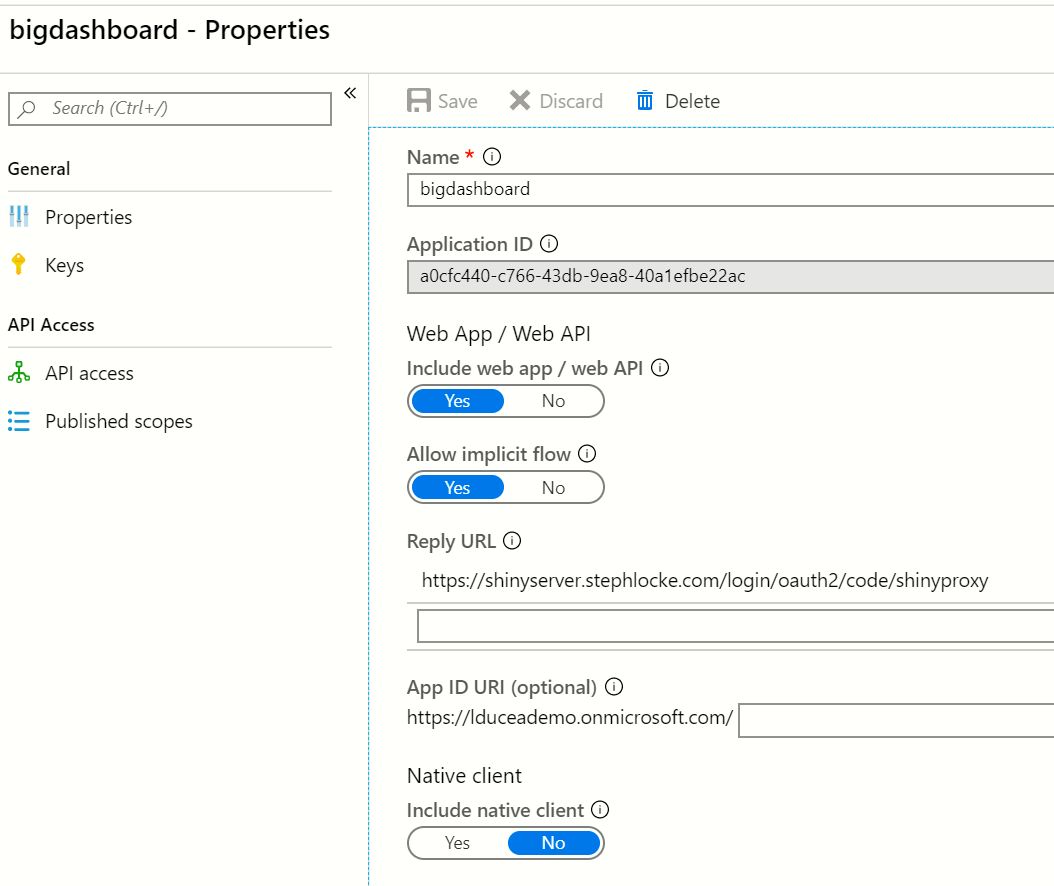
My application.yml includes
openid:
auth-url: https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/authorize
token-url: https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/token
jwks-url: https://login.microsoft.com/common/discovery/keys
logout-url: https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/logout&post_logout_redirect_uri=https://shinyserver.stephlocke.com
client-id: a0cfc440-c766-43db-9ea8-40a1efbe22ac
Weirdly, when I’m authenticating I’m getting errors because the return uri doesn’t match.
I can see in the url being created that it’s got http in it.
https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/authorize?response_type=code&client_id=a0cfc440-c766-43db-9ea8-40a1efbe22ac&scope=openid%20email&state=m6lDr6hJT5NOdazV5jo525r3OoAz-UtFHB_EynUhvxs%3D&redirect_uri=http://shinyserver.stephlocke.com/login/oauth2/code/shinyproxy
Is the http something that’s added/configurable on the shinyproxy side?
PS If I need to do this forward headers thing, is this nested in proxy or is it meant to go in the yaml at the same hierarchy level as proxy? https://www.shinyproxy.io/security/#https-ssl-tls
Lol, with forward headers at the top level I now get 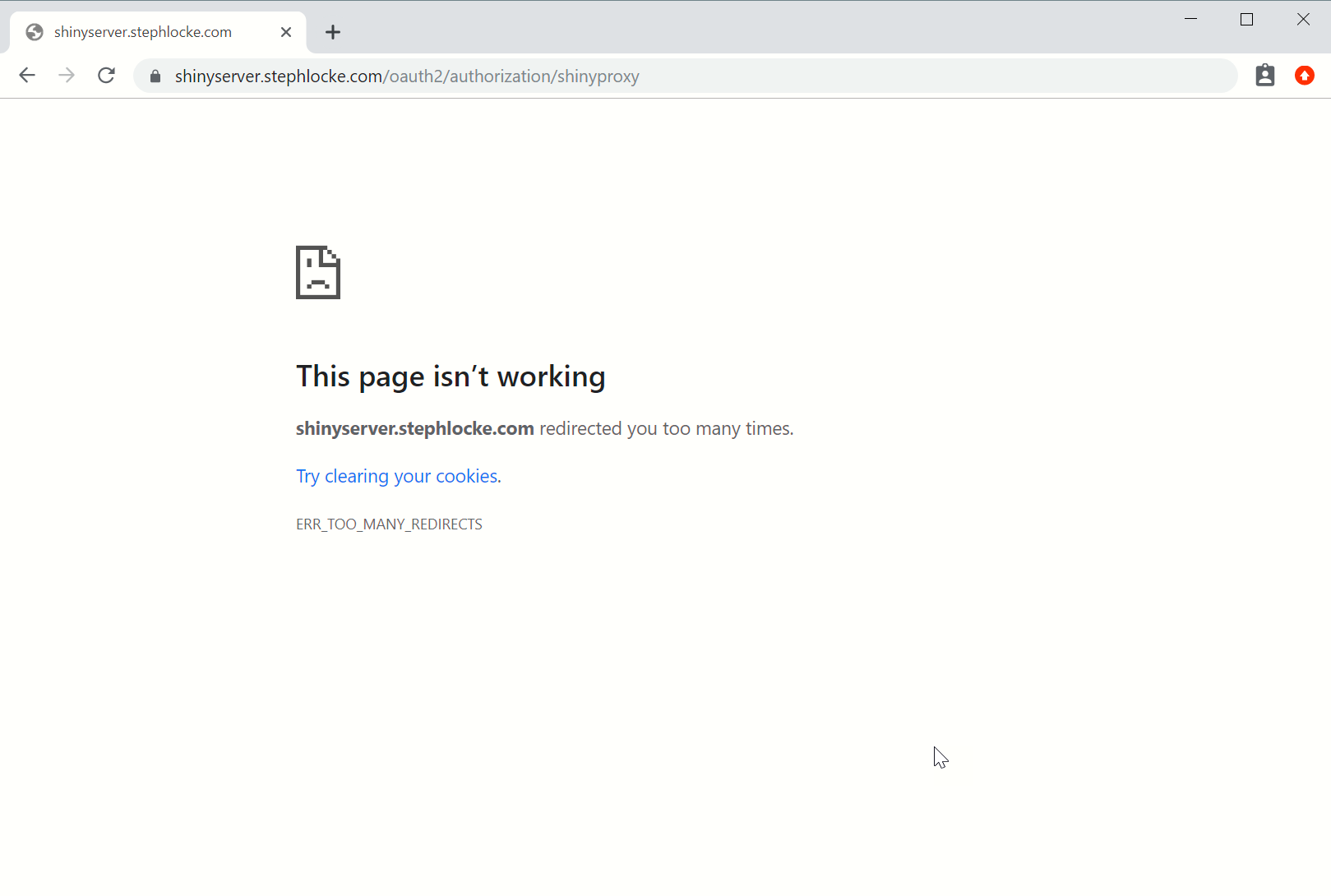
My ingress looks like:
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: shinyproxy
annotations:
kubernetes.io/ingress.class: "nginx"
cert-manager.io/issuer: "letsencrypt-prod"
spec:
tls:
- hosts:
- shinyserver.stephlocke.com
secretName: dnsftw2
rules:
- host: shinyserver.stephlocke.com
http:
paths:
- backend:
serviceName: shinyproxy
servicePort: 80
path: /
Looks like the redirect issue is due to not receiving the email. I’ve created a user flow which will return the email. Next step - working out how to change the auth urls in the application!
#GettingThere 
Eep, stackoverflow on the latest config
openid:
auth-url: https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/B2C_1_signinonly/oauth2/v2.0/authorize
token-url: https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/token
jwks-url: https://login.microsoft.com/common/discovery/keys
logout-url: https://login.microsoft.com/lduceademo.onmicrosoft.com/oauth2/logout?p=B2C_1_signinonly&post_logout_redirect_uri=https://shinyserver.stephlocke.com
client-id: a0cfc440-c766-43db-9ea8-40a1efbe22ac
Result:
2019-10-23 12:45:18.490 ERROR 1 --- [ XNIO-2 task-4] io.undertow.request : UT005023: Exception handling request to /login/oauth2/code/shinyproxy
java.lang.StackOverflowError: null
at java.security.AccessController.doPrivileged(Native Method) ~[na:1.8.0_232]
at sun.net.www.protocol.http.HttpURLConnection.<init>(HttpURLConnection.java:876) ~[na:1.8.0_232]
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.<init>(AbstractDelegateHttpsURLConnection.java:55) ~[na:1.8.0_232]
at sun.net.www.protocol.https.DelegateHttpsURLConnection.<init>(DelegateHttpsURLConnection.java:64) ~[na:1.8.0_232]
at sun.net.www.protocol.https.HttpsURLConnectionImpl.<init>(HttpsURLConnectionImpl.java:100) ~[na:1.8.0_232]
at sun.net.www.protocol.https.Handler.openConnection(Handler.java:62) ~[na:1.8.0_232]
Revised the URLs per info at https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/B2C_1_v1signinonly/v2.0/.well-known/openid-configuration
openid:
auth-url: https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/b2c_1_v1signinonly/oauth2/v2.0/authorize
token-url: https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/b2c_1_v1signinonly/oauth2/v2.0/token
jwks-url: https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/b2c_1_v1signinonly/discovery/v2.0/keys
logout-url: https://lduceademo.b2clogin.com/lduceademo.onmicrosoft.com/b2c_1_v1signinonly/oauth2/v2.0/logout
client-id: a0cfc440-c766-43db-9ea8-40a1efbe22ac
client-secret: 'xxx'
With logs like https://gist.github.com/stephlocke/7dc645e3f986a1fa3bcc060de42c841a
The policy returns email in the response. If I don’t put any group restrictions into the solution, should it work for everyone and redirect to the login page?
same problem here using openid with active directory and nginx for https
already added the option
server:
useForwardHeaders: true
but doesnt work…
1 Like
I’m having the same issue. I have also tried:
server:
forward-headers-strategy: framework
…and…
server:
forward-headers-strategy: true
1 Like
Hi @John_Poirier
Are you sure put the server property at the top level of the application.yml file? It should not be places under proxy, but really at the same level as proxy.
1 Like
I had this same problem behind a reverse proxy and eventually just loaded the SSL keys into the shinproxy container. This seems like not the most elegant way to solve the problem, but it worked.


