I got two security related questions from a security auditor.
#1 - X-Frame-Options header is not included in the HTTP response to protect against ‘ClickJacking’ attacks
#2 - A cookie has been set without the secure flag, which means that the cookie can be accessed via unencrypted connections.
Based on the shinyproxy documnent, I can address these two questions by including in application.yml the config specs like
server:
secure-Cookies: true
frame-Options: sameorigin
Any one to confirm?
Thank you in advance.
Hi
This are almost the correct settings, you should use:
server:
secure-Cookies: true
frameOptions: sameorigin
You should not use a - in the frameOptions setting (I’ll fix this in the docs).
You can confirm that these options are correctly applied by:
- open the developer tools of your browser (e.g. using F12)
- go to storage tab (in Firefox)
- check the cookies:
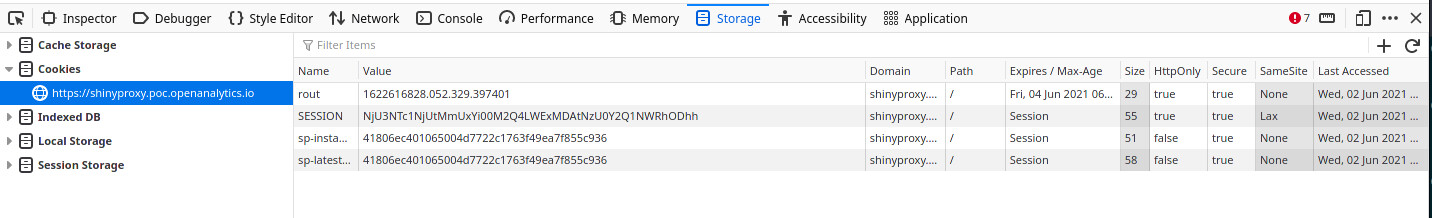
- as you can see both the secure and httponly flags are set
- to check the header, go to the network tab and reload the page
- look at the top-most request:
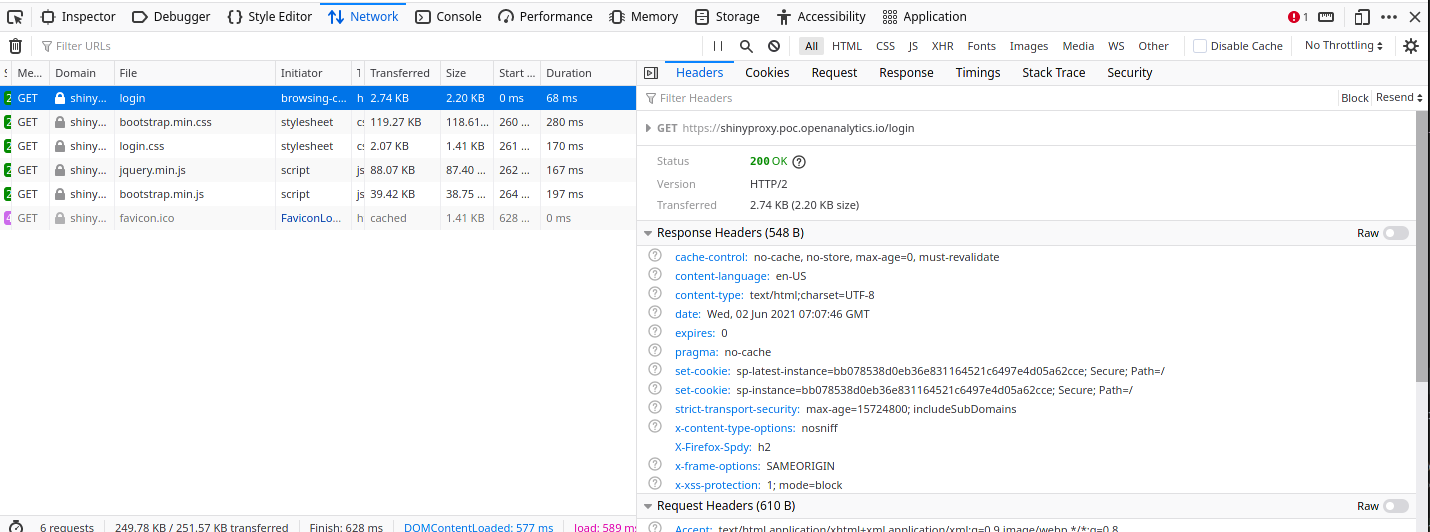
Thank you tdekoninck,
one more question about samesite attribute for cookie.
if I want to set samesite attribute for cookie to ‘lax’ or ‘strict’, should I change like beow?
proxy:
same-site-cookie: lax
or
proxy:
same-site-cookie: strict
I can’t find documentation on available values other than none option.
proxy:
same-site-cookie: none
Thank you!
Hi
You should be able to pass Strict , Lax and None as values to that setting. However, please note that this setting does not apply to the session cookie set by ShinyProxy. (so only cookies created e.g. for SAML). We could easily introduce another option to set the same-site policy of the session cookie if needed.

