Hi @adanba
Thanks a lot for your response and questions. They made me having idea what should I do.
I had no idea what version of keycloak to use. I was trying to run quay.io/keycloak/keycloak image and it was new versions. Then, I tried to run old versions but there were some problems I couldn’t understand. After your response, I tried another docker image and ran container successfully. I used this jboss/keycloak image.
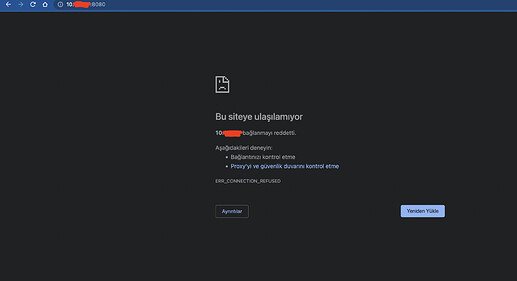
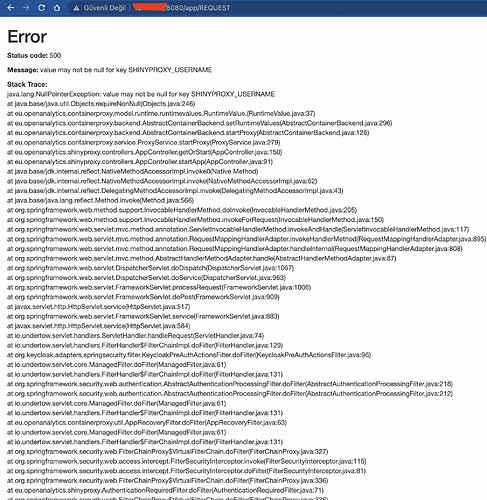
I achieved to assemble Shinyproxy and Keycloak successfully. On Keycloak, I created a new realm as shinyproxy and I created users and groups. Also I assigned the users to each group where they belong to. After these configurations, I can connect to shinyproxy on Keycloak right now. Shinyproxy opens with its landing page and it shows me the shiny apps, however when I want to run any of app I get this error.
Error
Status code: 500
Message: value may not be null for key SHINYPROXY_USERNAME
There is still lots of things I will learn. I created user and groups on keycloak but I didn’t make any changes in application.yml. Probably, this is the main reason. I should figure out how to assing user and groups to specific apps.
Here is my application.yml
proxy:
title: Shinyproxy
landing-page: /
favicon-path: /ShinyApps/LandingPage/favicon.ico
template-path: ./templates/modified_navbar
heartbeat-rate: 10000
heartbeat-timeout: 600000
container-wait-time: 20000
port: 8080
default-max-instances: 10
stop-proxies-on-shutdown: false
recover-running-proxies: true
recover-running-proxies-from-different-config: true
authentication: keycloak
keycloak:
realm: shinyproxy
auth-server-url: http://*.*.*.*:8787/auth
resource: shinyproxy
credentials-secret: gMHrFanXYkS7Szhr4TLILbhKqprOhn0I
admin-groups: [admin]
docker:
cert-path: /FBCert
url: http://localhost:2375
port-range-start: 20000
port-range-max: 20030
specs:
- id: REQUEST
display-name: App1
description: App1
logo-url: file:///ShinyApps/LandingPage/fbm.jpg
container-image: image/app1
max-lifetime: 120
container-cmd: ["R", "-e", "shiny::runApp('/root/App1/app.R', port = 3838, host = '0.0.0.0')"]
container-volumes: ["/Volumes/App1/BOR:/root/App1/reports/BOR"]
- id: App2
display-name: App2
description: App2
logo-url: file:///ShinyApps/LandingPage/fbm.jpg
container-image: image/app2
max-lifetime: 120
container-cmd: ["R", "-e", "shiny::runApp('/root/App2/app.R', port = 3838, host = '0.0.0.0')"]
container-volumes: []
container-log-path: /etc/shinyproxy/logs/container-logs
logging:
file:
name: /etc/shinyproxy/logs/shinyproxy.log
level:
org.keycloak: debug
spring:
servlet:
multipart:
max-file-size: 200MB
max-request-size: 200MB
server:
useForwardHeaders: true
For beginners like me 
Also I would like to explain all steps for beginners like me. I hope it will help people.
First of all, I had installed shinyproxy and postgresql on ubuntu server manually. They work fine. I just needed Keycloak to manage authentication.
In addition, I created a new DB named Keycloak on postgres. There must be a DB connection in Keycloak. That’s why I have to set DB environment variables for docker container . Then, I tested this connection and it ran succesfully.
You can see the code below. It will work for you, if DB runs.
docker run -d -p 8787:8080 -e DB_VENDOR=postgres -e DB_USER=postgres -e DB_PASSWORD=password -e DB_ADDR=*.*.*.* -e DB_PORT=5432 -e DB_DATABASE=Keycloak -e KEYCLOAK_USER=admin -e KEYCLOAK_PASSWORD=admin jboss/keycloak
When the container created successfully, you can go to Keycloak page by using IP + Port info.
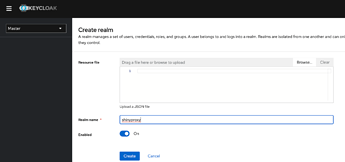
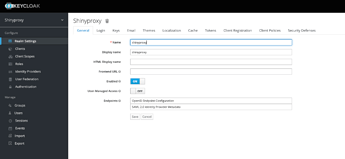
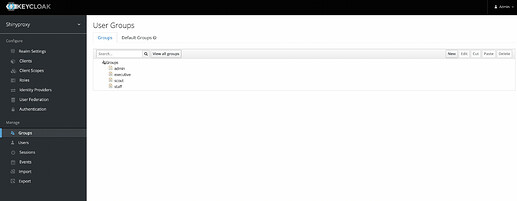
I created a new realm as shinyproxy.
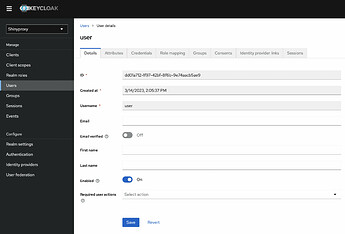
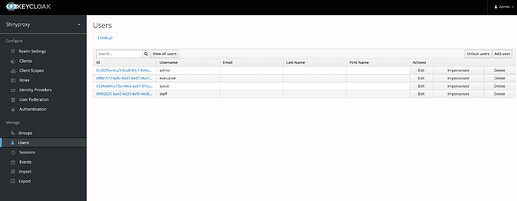
I created users and groups. Also I assigned the users to each group where they belong to.
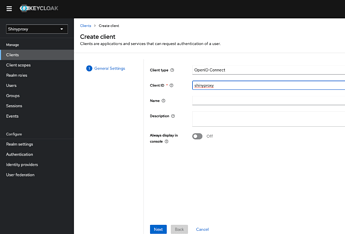
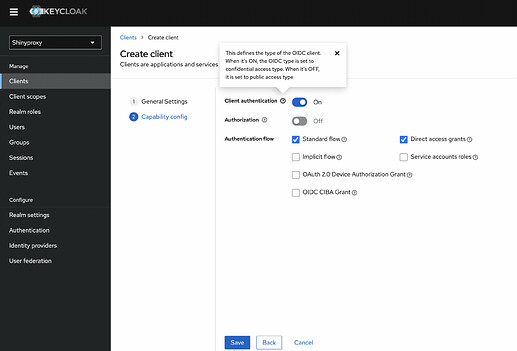
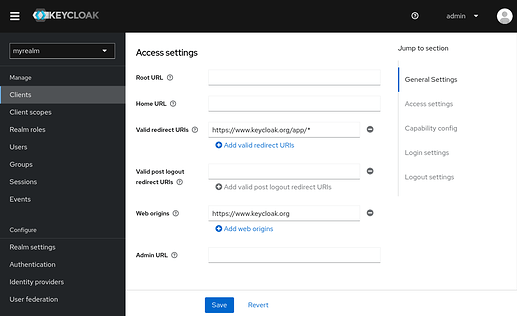
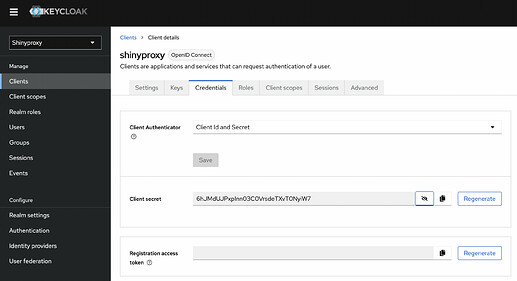
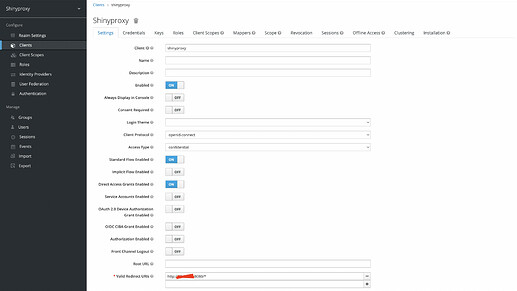
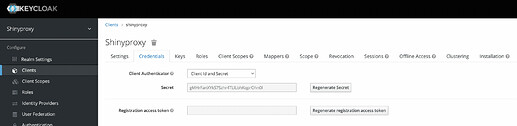
As final step, I created a client on Keycloak. I defined Valid Redirect Urls and got credential secret.
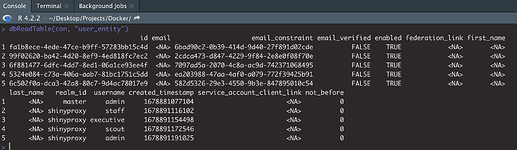
Also you can check DB connection between postgres and keycloak on Rstudio.
library(RPostgres)
con <- dbConnect(RPostgres::Postgres(),
host = "*.*.*.*",
port = 5432,
dbname = "Keycloak",
user = "postgres",
password = "password")
sort(dbListTables(con))
dbReadTable(con, "user_entity")
After these configurations, you will be able to have your login page.